Page 78 - The-5th-MCAIT2021-eProceeding
P. 78
2. Methodology
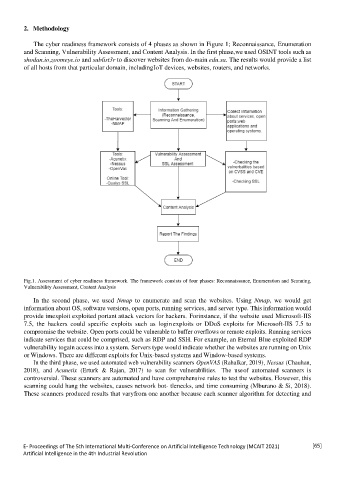
The cyber readiness framework consists of 4 phases as shown in Figure 1; Reconnaissance, Enumeration
and Scanning, Vulnerability Assessment, and Content Analysis. In the first phase, we used OSINT tools such as
shodan.io,zoomeye.io and sublist3r to discover websites from do- main edu.sa. The results would provide a list
of all hosts from that particular domain, including IoT devices, websites, routers, and networks.
Fig.1. Assessment of cyber readiness framework. The framework consists of four phases: Reconnaissance, Enumeration and Scanning,
Vulnerability Assessment, Content Analysis
In the second phase, we used Nmap to enumerate and scan the websites. Using Nmap, we would get
information about OS, software versions, open ports, running services, and server type. This information would
provide imexploit exploited portant attack vectors for hackers. For instance, if the website used Microsoft-IIS
7.5, the hackers could specific exploits such as login exploits or DDoS exploits for Microsoft-IIS 7.5 to
compromise the website. Open ports could be vulnerable to buffer overflows or remote exploits. Running services
indicate services that could be comprised, such as RDP and SSH. For example, an Eternal Blue exploited RDP
vulnerability to gain access into a system. Servers type would indicate whether the websites are running on Unix
or Windows. There are different exploits for Unix-based systems and Window-based systems.
In the third phase, we used automated web vulnerability scanners OpenVAS (Rahalkar, 2019), Nessus (Chauhan,
2018), and Acunetix (Erturk & Rajan, 2017) to scan for vulnerabilities. The use of automated scanners is
controversial. These scanners are automated and have comprehensive rules to test the websites. However, this
scanning could hang the websites, causes network bot- tlenecks, and time consuming (Mburano & Si, 2018).
These scanners produced results that vary from one another because each scanner algorithm for detecting and
E- Proceedings of The 5th International Multi-Conference on Artificial Intelligence Technology (MCAIT 2021) [65]
Artificial Intelligence in the 4th Industrial Revolution