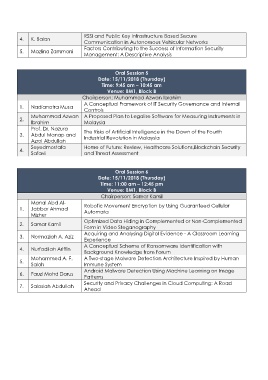
Page 3 - CRC2018ProgramBook_081118_final
P. 3
RSSI and Public Key Infrastructure Based Secure
4. K. Balan
Communication in Autonomous Vehicular Networks
Factors Contributing to the Success of Information Security
5. Mazlina Zammani
Management: A Descriptive Analysis
Oral Session 5
Date: 15/11/2018 (Thursday)
Time: 9:45 am – 10:45 am
Venue: BM1, Block B
Chairperson: Muhammad Azwan Ibrahim
A Conceptual Framework of IT Security Governance and Internal
1. Nadianatra Musa
Controls
Muhammad Azwan A Proposed Plan to Legalise Software for Measuring Instruments in
2.
Ibrahim Malaysia
Prof. Dr. Nazura
3. Abdul Manap and The Risks of Artificial Intelligence in the Dawn of the Fourth
Industrial Revolution in Malaysia
Azrol Abdullah
Seyedmostafa Home of Future: Review, Healthcare Solutions,Blockchain Security
4.
Safavi and Threat Assessment
Oral Session 6
Date: 15/11/2018 (Thursday)
Time: 11:00 am – 12:45 pm
Venue: BM1, Block B
Chairperson: Samar Kamil
Manal Abd Al-
1. Jabbar Ahmad Robotic Movement Encryption by Using Guaranteed Cellular
Automata
Mizher
Optimized Data Hiding in Complemented or Non-Complemented
2. Samar Kamil
Form in Video Steganography
Acquiring and Analysing Digital Evidence - A Classroom Learning
3. Normaziah A. Aziz
Experience
A Conceptual Scheme of Ransomware Identification with
4. Nurfadilah Ariffin
Background Knowledge from Forum
Mohammed A. F. A Two-stage Malware Detection Architecture Inspired by Human
5.
Salah Immune System
Android Malware Detection Using Machine Learning on Image
6. Fauzi Mohd Darus
Patterns
Security and Privacy Challenges in Cloud Computing: A Road
7. Salasiah Abdullah
Ahead