Page 183 - The-5th-MCAIT2021-eProceeding
P. 183
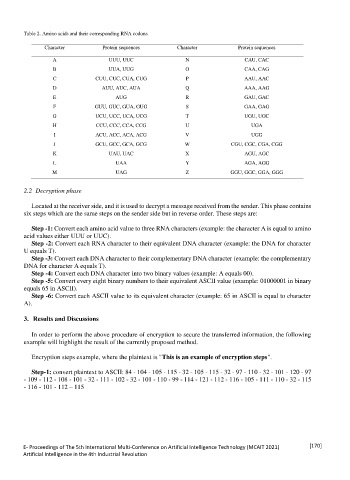
Table 2. Amino acids and their corresponding RNA codons
Character Protein sequences Character Protein sequences
A UUU, UUC N CAU, CAC
B UUA, UUG O CAA, CAG
C CUU, CUC, CUA, CUG P AAU, AAC
D AUU, AUC, AUA Q AAA, AAG
E AUG R GAU, GAC
F GUU, GUC, GUA, GUG S GAA, GAG
G UCU, UCC, UCA, UCG T UGU, UGC
H CCU, CCC, CCA, CCG U UGA
I ACU, ACC, ACA, ACG V UGG
J GCU, GCC, GCA, GCG W CGU, CGC, CGA, CGG
K UAU, UAC X AGU, AGC
L UAA Y AGA, AGG
M UAG Z GGU, GGC, GGA, GGG
2.2 Decryption phase
Located at the receiver side, and it is used to decrypt a message received from the sender. This phase contains
six steps which are the same steps on the sender side but in reverse order. These steps are:
Step -1: Convert each amino acid value to three RNA characters (example: the character A is equal to amino
acid values either UUU or UUC).
Step -2: Convert each RNA character to their equivalent DNA character (example: the DNA for character
U equals T).
Step -3: Convert each DNA character to their complementary DNA character (example: the complementary
DNA for character A equals T).
Step -4: Convert each DNA character into two binary values (example: A equals 00).
Step -5: Convert every eight binary numbers to their equivalent ASCII value (example: 01000001 in binary
equals 65 in ASCII).
Step -6: Convert each ASCII value to its equivalent character (example: 65 in ASCII is equal to character
A).
3. Results and Discussions
In order to perform the above procedure of encryption to secure the transferred information, the following
example will highlight the result of the currently proposed method.
Encryption steps example, where the plaintext is "This is an example of encryption steps".
Step-1: convert plaintext to ASCII: 84 - 104 - 105 - 115 - 32 - 105 - 115 - 32 - 97 - 110 - 32 - 101 - 120 - 97
- 109 - 112 - 108 - 101 - 32 - 111 - 102 - 32 - 101 - 110 - 99 - 114 - 121 - 112 - 116 - 105 - 111 - 110 - 32 - 115
- 116 - 101 - 112 – 115
E- Proceedings of The 5th International Multi-Conference on Artificial Intelligence Technology (MCAIT 2021) [170]
Artificial Intelligence in the 4th Industrial Revolution